The Ultimate Guide To WordPress Security – 2021

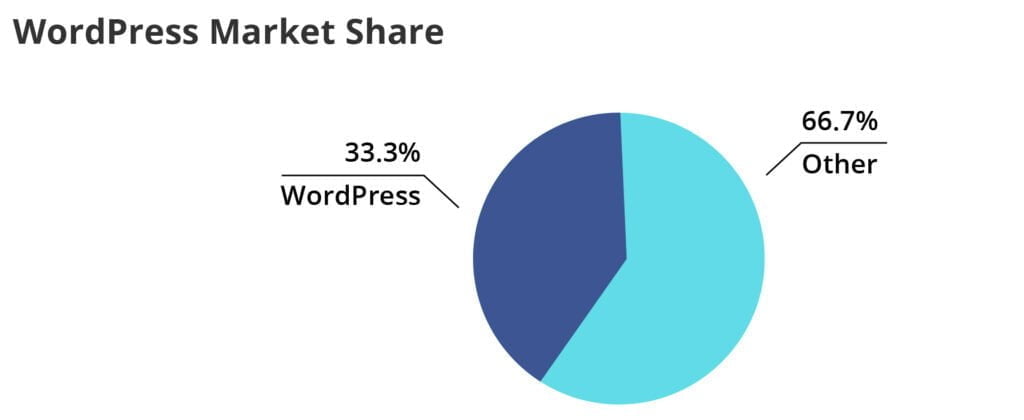
It’s widely known that WordPress is the most popular Content Management System on the planet, in fact over 33.3% off all websites hosted worldwide are run on WordPress. What might surprise people however, is the sheer amount of hacking attempts to WordPress websites every day.
Hackers target WordPress websites both big and small, with over 90,000 attacks happening every minute! While WordPress attacks are becoming more and more common, fortunately there are many steps you can take to help secure your website against attacks and malicious activity.
In this blog post we aim to guide you through everything related to WordPress security – from understanding why WordPress sites are hacked, to how you can secure your website, and even how you can fix a hacked WordPress website. Following this guide and taking in the basic principles of WordPress security will give you the best chance possible of protecting yourself against an account compromise.
Is WordPress Secure?

The short answer is – Yes
If you download a core WordPress installation with a good hosting provider, install a secure theme from a reputable source, use secure verified plugins, keep it updated, and use secure account credentials – you’re unlikely to see your website being hacked.
New WordPress versions can occasionally come with their own security issues and backdoors, however the team over at WordPress are usually very quick to rectify this.
What cannot be accounted for though is human behaviour, and extensions.
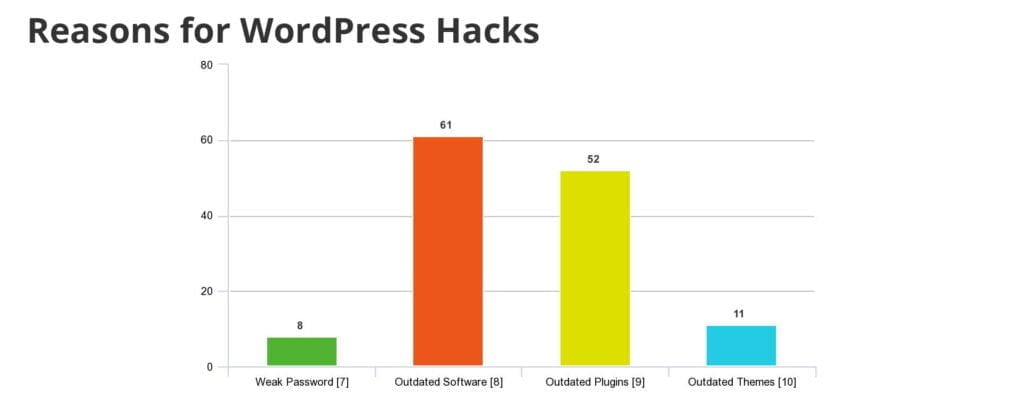
Simply put, the most common way of making your WordPress installation insecure is through human error (making mistakes), and through downloading plugins or themes. In the next part we will explain that in more detail and show you other reasons your WordPress installation can be targeted by hackers.
Why are WordPress sites targeted by hackers?
Due to the sheer popularity of WordPress, there’s a plethora of information available on why exactly hackers target WordPress websites. Regardless of your website’s size or nature, your website can still be targeted – at the end of the day, all websites are potential targets for hackers.
In general there are considered to be three main reasons for hacking a website: spamming, money, and hacktivism.
Spamming is a term that most people are familiar with in this day and age, whether you’ve been the victim of it or not. Essentially spamming means to send massive amounts of emails to lots of contacts from one or several email accounts. The intention of spamming is usually to spread malware, or for monetary gain – which feeds into the next reason.
Money is probably the most common reason for hacking a website. Hackers will often encrypt a compromised user’s files and then demand ransom from them for decrypting the files. Other methods of gaining money can be spamming from accounts on your website, or stealing sensitive information such as credit card information stored in your website’s databases. Businesses and consumers alike lose tens of billions of dollars every year to hackers!
Hacktivism is the final big reason hackers target WordPress websites. Sometimes hackers will have a particular political or social agenda, so they will hack public websites and deface them with messages supporting a particular party or influencing group. This has gotten more common and publicised in recent years.
Now that you have a better idea of why hackers target websites, you might be wondering – how exactly do they compromise websites?
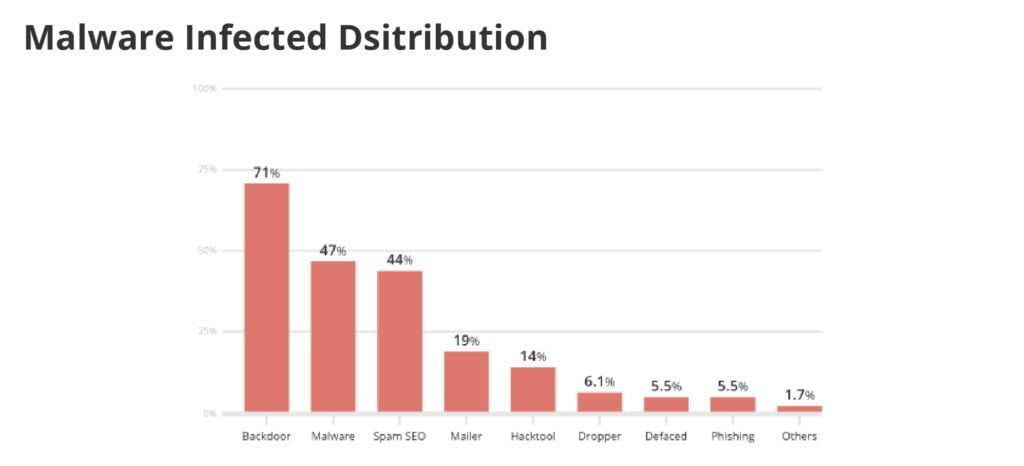
How can hackers compromise websites?

Writing code is a complicated task and it’s virtually impossible to create code with no security holes whatsoever, so it’s no surprise that hackers find and exploit vulnerabilities in WordPress so quickly.
Starting with the core WordPress software, a large portion of all hacked WordPress websites are running out-of-date software (or in other words, an older version of WordPress).
This is one of the key reasons you should always keep your WordPress installations up to date – because if you have an older version, hackers may have identified any security holes or backdoors, and can then easily exploit them to gain access to your website. While WordPress does rectify these quickly, more can pop up from time to time.
Another very common point of entry for hackers are the WordPress plugins, or themes. Outdated plugins and themes can present security vulnerabilities, just like the core WordPress files. Many plugins or themes can contain malicious code as well, which help the hacker gain entry to your website.
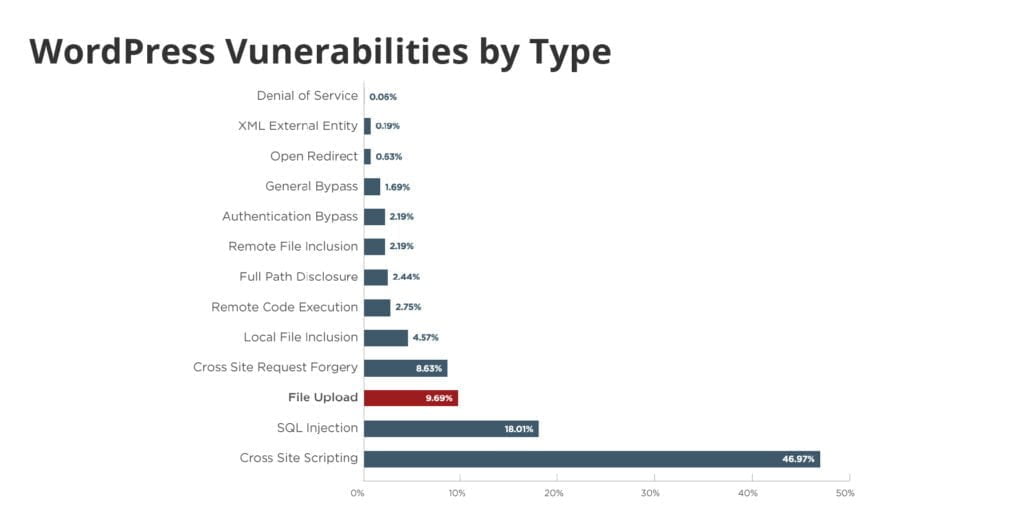
As well as the most obvious vulnerabilities created by human error such as weak passwords or insecure logins, there’s also a number of commonly exploited WordPress vulnerabilities including:
- SQL Injection (SQLI) – SQL Injection occurs when SQL queries and statements can be entered and executed from a website’s URL
- Denial of Service (DoS) – DoS attacks are when websites are brought offline by large, steady streams of traffic from hackbots
- Distributed Denial of Service (DDoS) – Similar to DoS attacks, except the traffic is coming from multiple different sources like infected routers or computers
- Cross-site Scripting (XSS) – XSS attacks are when hackers inject code into websites, often through input fields
- Brute Force – Brute force attacks are where hackers continuously try to login to the admin area with different combinations of usernames and passwords, bringing the site down
- File Upload – Hackers upload a file with malicious code to the server hosting the website, which is then executed
- Phishing pages – Websites or pages, which are created by a hacker, pose as legitimate websites while actually collecting user credentials or other sensitive information
- Malware – Malware is a malicious program or script with the purpose of infecting other websites or systems, and giving hackers access
- Authentication Bypass – A security hole which allows a hacker to bypass the login form on a website and gain access to the website
- Directory Traversal – Where a HTTP connection can be exploited to allow access to a site’s directories, as well as execute commands elsewhere on the server
WordPress security is a state of mind, not software

Before we get into the best practices in WordPress and how you can best secure your website against hackers, it’s important to remember that no matter how many plugins you install, or how much software you install, you still run the risk of getting hacked unless you understand that security is a state of mind that you need to adopt.
Taking extra steps to secure your website is pointless if you ignore the basic aspects of WordPress security.
By this we don’t mean that you have to sit around scanning your server every day for compromised websites.
What this statement means that before making additional changes to your WordPress installation, try and get used to keeping on top of things before they become an issue, and checking things properly before you install them.
For example, you should always try and make sure that your WordPress installations are updated as soon as new updates are released. Similarly, you should check plugin reviews and details before installing new plugins.
With that out of the way, let’s move on to the best practices when using WordPress.
WordPress security best practices

Now that we’ve covered why WordPress sites are targeted and how hackers compromise WordPress websites, let’s look at the best practices for WordPress security.
In this section we will explain in detail the things you should be trying to remember above all else – because remembering these basic principles will provide you with better protection against hackers than anything else will.
While many additional steps can be taken to secure your WordPress website against hackers, failing to remember these best practices will leave you wide open to attack.
As well as a bit of common sense, following these basic principles will help secure your WordPress website against any kind of attack.
Always keep updated
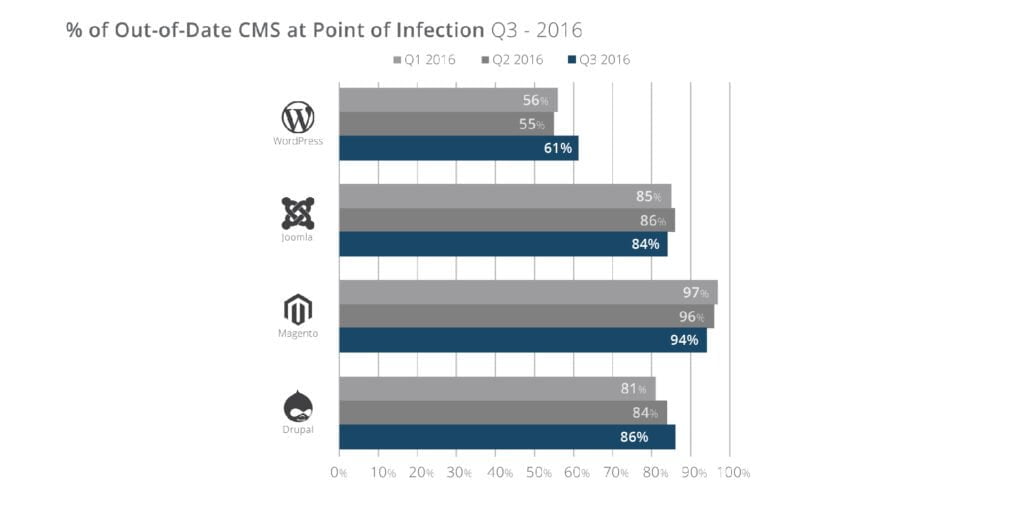
It might seem like common sense to some, but keeping your systems updated is often forgotten by a large portion of WordPress users. In fact, one of the most common causes of being hacked is having an outdated WordPress installation!
Older versions of WordPress can be more open to exploits that will have been secured in more recent versions, so it’s incredibly important to keep your WordPress installation updated. As soon as you’re aware of a new WordPress update install it to try and keep on top of any security holes.
Staying up to date doesn’t just apply to the core WordPress installation though. At some point you’ll inevitably need to install a different theme and plugins to extend the functionality of your website. As with the core WordPress installation, you should make sure you always have the latest version installed.
Use correct file permissions
File permissions in WordPress is something that many users don’t need to change at any point, however for various reasons the file permissions can sometimes be altered. With the wrong set of file permissions, you’re leaving yourself open to attack.
WordPress permissions should always be the following:
- 755 for all folders and sub-folders
- 644 for all files
Try and always make sure that you don’t make unnecessary changes to your file/folder permissions, and if you see that they are incorrect, revert them to the correct permissions.
Secure your login/user credentials
Another best practice to get used to is securing your login credentials for each user, as well as the administrator account. Around 20% of all hacked WordPress sites are hacked simply because the hacker obtained the login information for a WordPress user!
Giving someone access to the administrator WordPress account essentially gives someone complete control over your website, so it’s important to avoid that at all costs.
There are several basic steps you can take to secure your WordPress login:
- Don’t give anyone your login details – this might come as common knowledge, but it still happens! Make sure not to give anyone your login details for WordPress.
- Use strong passwords – many WordPress users have very simple passwords that can be guessed by hackers. Using a combination of uppercase and lowercase letters, as well as numbers and symbols, makes it harder for a hacker to guess your login details and helps protect you against account compromises
- Changing your Admin username – for several years now WordPress has stopped forcing users to have an administrator account named “admin”. Plenty of users still don’t change their administrator username which can make it easier for hackers to gain entry. When installing WordPress you should choose a username other than “admin” for your administrator account.
There are several other steps you can take related to logins and user credentials however since they require additional plugins or configuration, we will come back to that later on.
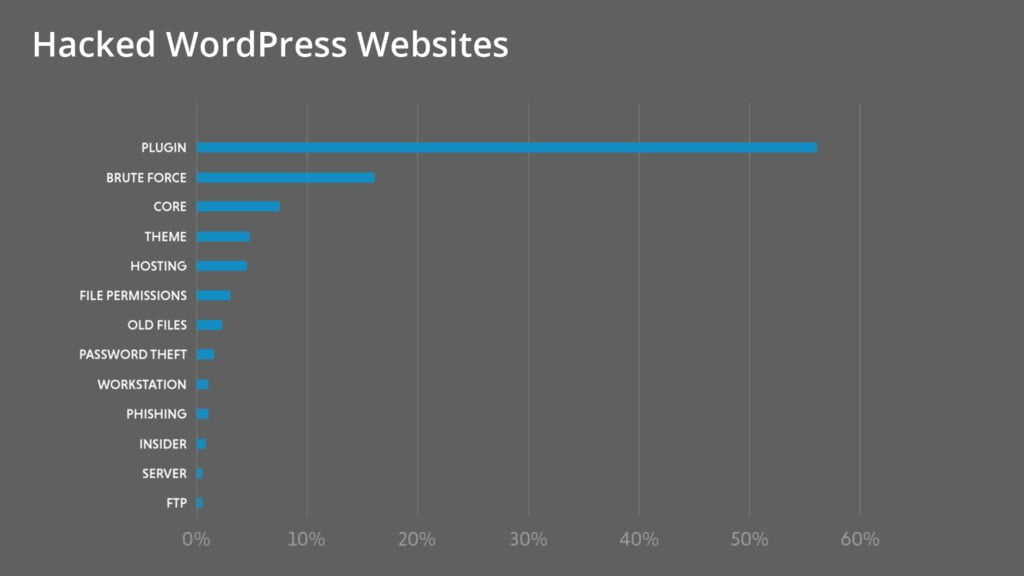
Follow good theme and plugin practices
Something you should get used to early on is following good practices with themes and plugins for your WordPress site.
One of the best things about WordPress is how easily it lets you add new plugins to your website, or change your website’s theme. Unfortunately this also presents a security issue, because plugin and theme vulnerabilities are so common, and because people install new themes or plugins often without thinking.
You don’t have to avoid installing any new plugins or themes to keep your website self, you should just make sure to remember a few simple things:
- Check for any known vulnerabilities – where possible try and check the plugin or theme for any known vulnerabilities. Reviewers will often point this out, but you can also use websites such as WPScan to check the plugin or theme.
- Read reviews – make sure not to ignore reviews of the plugin or theme you wish to download! Reviews are a good indicator of not only the plugin’s usefulness, but also any obvious security flaws or backdoors in the plugin or theme.
- Only use trusted sources – this is fairly self-explanatory. When downloading plugins or themes, try and make sure only to use official WordPress extensions or from trusted third party developers or marketplaces.
- Avoid using unsupported plugins/themes – you should always try and avoid installing any themes or plugins that are no longer supported by the developer. Lack of support means that any security vulnerabilities that are present won’t be patched out, and hackers can exploit them.
- Remove any unused plugins/themes – even if you’re not using a plugin, it’s still installed on your website meaning the code is still sitting on the server. This means that it can still be exploited by hackers.
With that we will move on to our final best practice for keeping your WordPress site secure.
Choose secure WordPress hosting
Before your WordPress website goes online, you’ll need to choose a hosting provider to host your website with. There are hundreds of hosting providers out there, but the hosting provider you have can make a big difference to your website’s security in general.
When looking for a web hosting provider, you want to look for a secure, ideally managed, WordPress hosting plan. There are several things to keep an eye out for in this regard.
First, if you’re on a shared hosting platform, you’ll want to try and ensure that your web hosting provider uses account isolation in their servers. Account isolation essentially means that your site is isolated from other websites being hosted on the same server, so your website can’t get infected when another website on the server is infected. Software such as CageFS can provide this kind of protection.
Other things to look for in a hosting provider include:
- Server optimisations – ideally try and choose a host which optimises their web hosting servers for WordPress performance and security
- Server-level firewalls – always choose a web hosting provider that configures a firewall (ideally WordPress-specific) at the server level
- Regular security scans – your hosting provider should be running security scans for malware and viruses regularly
A good WordPress hosting plan doesn’t just depend on the hosting provider itself however, it also varies with each WordPress hosting plan provided. Ideally you want to look for a secure, optimised WordPress plan with SSD storage and a high availability configuration like our new optimised WordPress hosting plans. Choosing a plan like this will ensure that your website can take advantage of the best performance available, as well as the latest and greatest in hosting technology.
Now that we’ve covered the best practices in WordPress security, let’s move on to the basic steps you can take to secure your WordPress website.
Basic WordPress Security Steps
After understanding the best practices for WordPress security, you may be wondering what basic steps you can take to protect your website from hackers.
In this section we’re going to show you how you can secure your website quickly and easily, with no difficult coding or configurations necessary!
Use a good security plugin
Security plugins are among the most common types of plugins available for WordPress, and for good reason.
Having a security plugin can provide a fantastic boost to your website’s security, especially when combined with other basic measures.
There’s a staggering range of security plugins available for WordPress, and some of them can actually reduce your website’s security! So it’s important to choose the right security plugin for your website.
Some of the best security plugins you can install include:
- Wordfence Security – possibly the widest used security plugin, with over 2 million installations. This free plugin provides comprehensive protection against most kinds of common WordPress attacks.
- All In One WP Security & Firewall – another very popular plugin with over 800,000 downloads, this plugin is also free and provides a great extra layer of security for your WordPress website.
- iThemes Security – this popular and easy-to-use plugin provides ample protection against most WordPress attacks with features including brute force protection, file change detection, and database backups
- Sucuri Security – this premium security plugin provides complete protection for your website with WAF protection, monitoring, and incident response features
If you’re installing a security plugin just remember to download it from a trusted source, and read the reviews first to make sure that it’s a legitimate plugin.
One of the best plugins we would recommend if you’re using Plesk Control Panel is the WordPress Toolkit. This plugin not only lets you install and manage all of your WordPress instances from one simple interface, it also helps secure your WordPress installations against any malicious activity. WordPress Toolkit features an inbuilt security scanner to automatically audit your WordPress files, as well as automated plugin and theme updates. A variety of other helpful features are also included such as maintenance mode, CLI access, debug management and much more.
Run regular security scans
It might seem like a bit of a hassle but at the end of the day, the sooner you recognise a security issue, the sooner you can deal with it.
By now you’ve probably realised that having some sort of security software at your disposal will be a great boost to your website’s protection. But if you’re not utilising this software properly, then what’s the point?
You should try and make sure to regularly scan your WordPress installation, including any associated files, user accounts, and databases, to identify any potential security threats before they become a bigger issue.
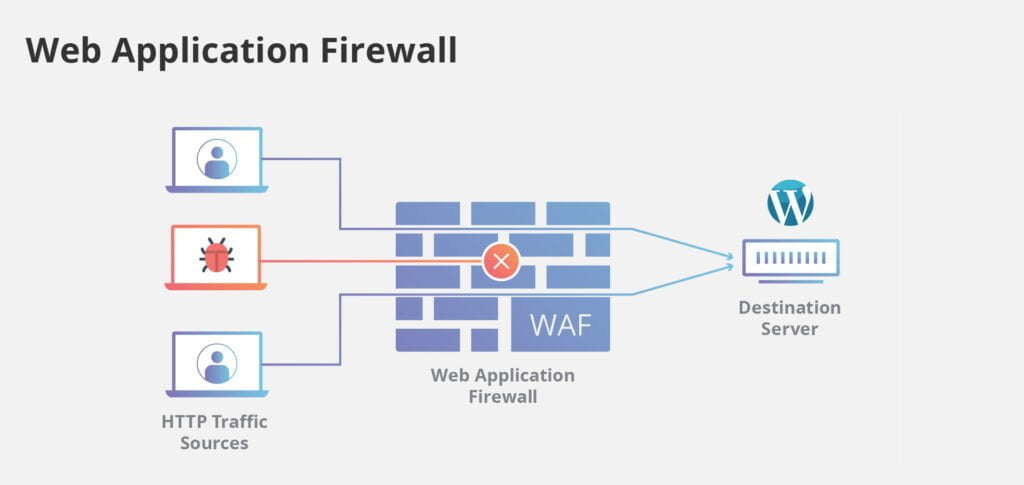
Enable a Web Application Firewall (WAF)
Similar to security plugins for WordPress, there’s a wide range of Web Application Firewall plugins which can help divert attacks before they reach your WordPress website. Some of the security plugins actually include a WAF as well!
A WAF is an application level firewall which applies a set of specific rules to each HTTP interaction, with the purpose of blocking any malicious traffic before it hits the website itself. Generally these rules prevent against common attacks such as SQL injection and cross-site scripting.
Some of the best WAF plugins include:
- Cloudflare – this robust web firewall also acts as a a performance optimisation tool as well as a content delivery network (CDN), to further help users in different geographic locations load the website more quickly.
- SiteLock – another well known security company providing a WAF which operates at the DNS level to block malicious traffic well before it hits your website and the server that your website is hosted on.
Backup your site regularly
Backing up your website is not only a good way of protecting against hackers, it also helps you get your website back online quickly if you’ve been the victim of hacking. Backups should be taken as regularly as possible, because you never know when a hacker will strike!
These days you can backup your WordPress site quickly and easily, so there’s no excuse not to!
Plugins can be used to backup your WordPress website more conveniently, but just make sure if you’re going down this route that you use a trusted plugin.
Manually backing up your WordPress website will involve taking backups of the website’s core WordPress files, theme files, and plugin files, as well as any additional content such as images, Javascript, or static web pages.
When backing up you also need to take backups of your WordPress website’s databases, including all posts, users, comments, categories etc.
Force your website to load with SSL/HTTPS
Forcing your website to load through HTTPS with an SSL certificate is a great way of protecting your website, and should be configured for every website you have as a minimum. HTTPS has many benefits, not limited to security.
HTTPS encrypts all communications between the visitor and the website, so hackers can’t intercept and snoop on the data being transmitted. Ensuring a secure connection can minimise the options hackers have for attacking your website so it’s always advisable to install an SSL certificate and force it to load through HTTPS.
Having a HTTPS connection will especially help with your login pages. Since the data being transmitted will be encrypted, hackers won’t be able to obtain your login details.
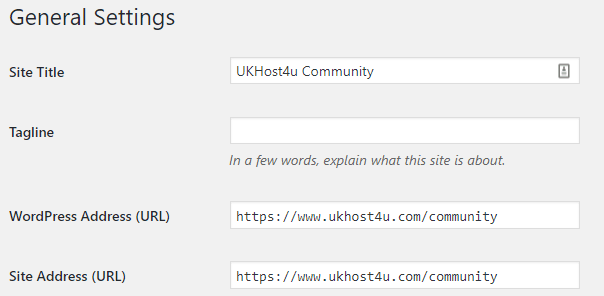
Once you’ve installed an SSL certificate, you first need to configure your site’s URL to load through HTTPS. This is done in Settings > General, through the WordPress dashboard:
Next, you need to add the following code to the .htaccess file (replacing yoursite.com with your website’s URL):
RewriteEngine onRewriteCond %{HTTP_HOST} ^yoursite.com [NC,OR]
RewriteCond %{HTTP_HOST} ^www.yoursite.com [NC]
RewriteRule ^(.*)$ https://www.yoursite.com/$1 [L,R=301,NC]
Finally, if you want to also force your dashboard pages to load through HTTPS, add the following line to the wp-config.php file:
define('FORCE_SSL_ADMIN', true);Advanced WordPress Security Steps
So now that we’ve covered the basic steps you can take to secure your WordPress website, let’s get into the more advanced measures to take.
In this section we’ll explain some of the more advanced or technically difficult measures you can take to secure your WordPress website.
Disable XML-RPC
XML-RPC is a feature used by WordPress for allowing users to post on WordPress blogs with external weblog clients like Windows Live Writer, as well as for connecting to the WordPress mobile application.
For a long time the XML-RPC service was disabled by default for security reasons, however since WordPress 3.5 XML-RPC has been enabled by default, with the option to disable it from the WordPress dashboard being removed.
XML-RPC presents a significant security risk as XML-RPC attacks are very common, so unless you absolutely need it you should disable it in your website.
You can disable XML-RPC in your WordPress website by entering the following code into your .htaccess file (located in the root directory of your website):
# Block WordPress xmlrpc.php requests <Files xmlrpc.php> order deny,allow deny from all allow from 123.123.123.123 </Files> <Files xmlrpc.php>
This can also be achieved by installing a XML-RPC disabler plugin if you don’t feel comfortable editing the .htaccess file.
Disable Directory Indexing & Browsing
By default most webservers such as Apache and NGINX have directory browsing enabled.
What this means is that people can view the contents of individual directories on your website, which allows hackers to easily find potential vulnerabilities or exploits in your themes and plugins.
You should always disable directory indexing and browsing, and luckily all you need to do is add a single line of code to your .htaccess file below the WordPress generated code:
Options -Indexes
Adding 2 Factor Authentication (2FA)
2 factor authentication, simply put, is an extra layer of authentication for logging into WordPress. It requires that you verify your account login, typically by SMS or mobile application, to prove that you’re logging in genuinely and not without authorisation.
Hackers will often use brute force attacks to try and guess your username and password to break into your site. They can then infect your website with malware.
With two factor authentication, even if someone has stolen your password they won’t be able to login unless they have your phone.
2FA can be added to WordPress through a number of different plugins such as:
- Google Authenticator – this official plugin from Google lets you authenticate your WordPress login by using an application for Android or iOS
- Unloq – this plugin is similar to Google Authenticator and works essentially the same
- Authy – this plugin allows you to authenticate your login with an SMS message, thereby avoiding the need to install a smartphone application
Limit login attempts
One relatively straightforward measure you can take to securing your WordPress website is to limit the amount of login attempts users can make when logging in.
Limiting login attempts can help prevent against brute force attacks, as hackers will be locked out of the system for a set period of time if they attempt to login more than a certain number of times.
Unfortunately WordPress doesn’t come with this feature built-in, however there’s a wide variety of easy to install plugins that you can use to achieve this:
- Loginizer – this is probably the most widely used login limiter plugin available. This plugin prevents against brute force attacks by using IP blacklists as well as features for 2FA and reCAPTCHA.
- WP Limit Login Attempts – as the name says, this plugin also limits login attempts and blacklists IP addresses
- Limit Login Attempts Reloaded – this plugin acts similarly to the other login attempts limiter plugins, with limited retry attempts and IP blacklisting
Auto update WordPress core
As you’ve probably gathered by this point, keeping WordPress core files updated is incredibly important for the security of your website.
Manually updating your WordPress installation frequently can be a bit of a hassle, but luckily you can easily set WordPress core files to automatically update whenever a new version is released!
All you need to do to add the following line to the wp-config.php file in your website’s root directory:
define( 'WP_AUTO_UPDATE_CORE', true );
WordPress core files aren’t the only thing you can set to automatically update, as we will learn next.
Auto update WordPress plugins & themes
As WordPress plugins and themes are often the point of entry for hackers, it makes sense that you should always keep them updated.
But manually updating all of your plugins and themes can be an arduous task.
Thankfully you can also set all of your WordPress plugins and themes to automatically update whenever a new version is released.
Setting this is straightforward as well, and just requires a few lines of code into the functions.php file in your base WordPress installation.
Setting automatic updates for plugins is done by adding the following line of code:
add_filter( 'auto_update_plugin', '__return_true' );
Settings automatic updates for themes is done by adding this line of code:
add_filter( 'auto_update_theme', '__return_true' );
Use .htaccess to limit what can be run

The .htaccess file is essential to the running of every website, WordPress or otherwise. This file controls the behaviour of a website when a user loads it into their browser, and contains redirects and WordPress generated code, among many other things. By default, the .htaccess file is located in the root directory of your website.
In the context of security in WordPress, the .htaccess file can be used to restrict your website’s access and secure what can or can’t be accessed.
There’s a lot of different changes you can make to your website’s .htaccess file, so we will only be detailing a few of the key changes you can make here.
Block IP addresses – the .htaccess file can be used to block any number of IP addresses, which is very useful for blocking bad bots or known malicious agents. The following code can be used to block any IP addresses:
# Block one or more IP address. # Replace IP_ADDRESS_* with the IP you want to block <Limit GET POST> order allow,deny deny from IP_ADDRESS_1 deny from IP_ADDRESS_2 allow from all </Limit>
Allow only selected file types in wp-content – the wp-content folder contains most of the plugins, themes, and media uploads, so you don’t want people to access it without restrictions. The .htaccess file can be used to block access to all file types other than the ones you specify, with the following code:
# Disable access to all file types except the following Order deny,allow Deny from all <Files ~ ".(xml|css|js|jpe?g|png|gif|pdf|docx|rtf|odf|zip|rar)$"> Allow from all </Files>
Restrict access to wp-config.php and .htaccess – the wp-config.php file contains the most sensitive access information on your WordPress site including database credentials and settings. To prevent access to the wp-config.php file you can use the following code:
# Deny access to wp-config.php file <files wp-config.php> order allow,deny deny from all </files>
And for the .htaccess files you can use the following:
# Deny access to all .htaccess files <files ~ "^.*\.([Hh][Tt][Aa])"> order allow,deny deny from all satisfy all </files>
Restrict all access to wp-includes – the wp-includes folder includes only the core files for wordpress, without any themes or plugins. As such, nobody should be able to access this folder or modify any files inside it. Use the following code to disable access to the wp-includes directory:
# Block wp-includes folder and files <IfModule mod_rewrite.c> RewriteEngine On RewriteBase / RewriteRule ^wp-admin/includes/ - [F,L] RewriteRule !^wp-includes/ - [S=3] RewriteRule ^wp-includes/[^/]+\.php$ - [F,L] RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L] RewriteRule ^wp-includes/theme-compat/ - [F,L] </IfModule>
Allow only selected IP addresses to access wp-admin – the wp-admin folder contains the files needed to run the WordPress dashboard, so your users don’t usually need access to this folder (unless creating an account). To limit the access to the wp-admin area to certain IP addresses, use the following code:
# Limit logins and admin by IP <Limit GET POST PUT> order deny,allow deny from all allow from 302.143.54.102 allow from IP_ADDRESS_2 </Limit>
Data Centre Security
Several steps can be taken to increase security for WordPress at the data center level. While you likely don’t have access to implement these changes in the data centre that’s hosting your website, if you’re looking for a hosting provider you can try and make sure that their data centre is equipped to protect against incoming attacks. As a minimum, your provider should ensure that they have a system in place to route their incoming traffic through a cloud-based Web Application Firewall (WAF) before arriving at the servers, in order to block any incoming attacks before they reach your website. Another measure that can be taken to secure your data centre is to provide protection in the form of Distributed Denial of Service (DDoS) mitigation. In the case that someone attempts to DDoS your server, you’ll then be protected against this without having to take further action.
Server (OS) Level Security
At the Operating System level there are several measures you can take to increase your protection against WordPress attacks. As a minimum, you should make sure you keep everything updated to the latest release – this includes the kernel, and the operating system itself, as well as any additional system software updates. You should try and ensure that your users are utilising strong passwords to prevent against brute access attacks. On the firewall, it’s advisable that you close all non-essential ports to prevent against any configuration issues or bugs. Ensure that you’re using a virus scanning software of some kind to automatically scan your server regularly for any viruses or malware. Lastly, if possible you should employ software to automatically scan your server regularly for any compromises or vulnerabilities in software.
Web Server Level Security
Another layer at which you can make significant efforts to protect your WordPress website is at the web server layer. As with the OS and data center layers, you should make sure to employ some kind of WAF to protect yourself from incoming attacks. Forcing usage of strong passwords is also advisable at the web server level. If you’re using Apache in a shared hosting environment, then you should try and make sure that any insecure Apache modules such as mod_perl are removed, to reduce the risk of cross-client access. When managing users, you should also ensure that any unnecessary login options that you don’t need or support are disabled on your server.
What should I do if my site has been hacked?
The sad reality about hosting any kind of WordPress website is that no matter how much time you put into securing your website, there’s still a chance your website could be hacked.
Having your website hacked can indeed be a very stressful ordeal, not to mention to impact it can have on your business and visitor experience. It can truly be a nightmare to deal with at times, however attacks are so common that it’s important to know how to deal with them.
Luckily dealing with a hacked WordPress website doesn’t need to be as hard as you think it might be!
Before fixing the hacked website, there’s a few steps you should take.
1. Get your site back online
First things first – you’ll need to get your website back online. This is especially crucial if you’re running an Ecommerce website, as you don’t want to lose crucial business!
Getting your website back online can sometimes be difficult but usually removing a few suspect files or lines of code will get your website back online.
Thankfully, your web hosting provider can usually assist you with getting your website online, so when you’ve been hacked one of the first things you should do is inform your hosting provider.
2. Identify point of entry or weakness
Once your website is online you can focus on identifying the area of the website that allowed the hacker to gain access, or in other words, the security hole in your website.
Most of the time this is caused by outdated or insecure plugins or themes, so you should check first that all of your themes and plugins are updated to the latest version. It’s also worth checking that the core version of WordPress is updated to the latest version too.
Another major cause is having insecure plugins or themes, so check that all of your plugins and themes are legitimate, and in use! Delete any plugins that aren’t being used.
3. Install a security plugin
By this point you have probably already realised that installing a security plugin is a good decision (and if you haven’t, then you haven’t been reading properly!).
If you’ve not already installed one, then it’s time to find a good security plugin and install it!
See our list of good security plugins to choose from.
As well as helping you rescue any website that might have been hacked, having a good security plugin will help prevent it from occurring again in the future.
4. Scan for malware
Now that you have a good security plugin you can start working on getting rid of the problem.
Start with running a security scan for any malware that’s still present on your account, in any files or directories. The security plugin should be able to pick up any suspicious content and remove it for you, so this is usually relatively straightforward.
With that we can move on to actually fixing the hacked WordPress website.
How can I fixed my hacked WordPress website?
After getting your website back online and getting rid of any malware present, you can properly clear out anything that was added to your website or changed as a result of the account compromise.
Depending on the scale of the website hack, this stage can be long and you may need some assistance from your web hosting provider, so don’t hesitate to get in touch with their support team.
1. Remove suspicious users
The first thing you should check on your website is the users that have been created on your website.
Often when a hacker gains access to a website, they will create their own user so that they can access and manipulate files inside the website structure. You don’t want this for obvious reasons, so you should review all users that have access to the website’s files and directories.
You should only have users for those that absolutely need them, with the relevant permissions set for them. If you see any users that shouldn’t be there, delete them immediately to avoid any further account compromises.
2. Reset all passwords
Sometimes when a hacker has access to your website, it’s because they’ve obtained login details for yourself or another user.
As a precaution, you should reset passwords for every user account you have on the website. If they have obtained your password, then it’s possible that they’ve also obtained the passwords of other user accounts.
When setting a new password make sure that you are using strong passwords with a combination of uppercase and lowercase letters, as well as numbers and symbols where possible.
3. Restore corrupted files
When your website’s been hacked, the hacker may have corrupted the core WordPress files that you have.
You’re going to need these files for your website to run, so it’s imperative that you replace any corrupted WordPress files on your website to the base version.
You’ll first need to download the core WordPress files from their official website
Once you have the correct files, you just need to replace the corrupted files with the new ones via FTP or a file manager in your hosting provider’s control panel of choice.
4. Remove suspicious database entries
Another area which hackers will often add malicious content into is the databases.
As with the users and files, you should audit all databases that your website uses, so that you can identify any suspicious database entries. Often hackers will enter data which they can use to further manipulate your website or gain sensitive information themselves.
Any database entries that shouldn’t be there, delete immediately to avoid any further damage.
5. Check WordPress core file integrity
If you haven’t needed to replace the core WordPress files yet, then it’s a good idea to check the integrity of the files.
Often it will be obvious if your WordPress core files have been altered, however sometimes it can be more difficult to spot.
A telltale sign is if the file has been modified recently, or at a different date to the other core WordPress files. The last modified attribute should tell you that.
There are also several other ways of checking the integrity of your core WordPress files. Checksums can be used to verify the integrity of WordPress files, with many PHP scripts available online which check the md5sum of the WordPress core files to see if they are correct.
6. Check audit logs for any altered files
The final step you should take to fix your WordPress website is to check your website’s audit logs to see if any of your other files have been altered at all.
You should have access to your website’s audit logs but if you’re unsure of where these are, you can always ask your hosting provider who should be able to point you in the right direction.
Look for any files that were modified on dates you don’t recognise, or by users you don’t recognise – as those are tell-tale signs of malicious activity.
How can I prevent being hacked again?
So, with your website back online, rid of any malware, and fixed from any corrupted files – what’s next?
Well, the short answer to this is that you need to harden your WordPress website!
Undoubtedly you don’t want this to happen again, so as well as taking the steps we’ve listed earlier on in this article, you should also consider taking some extra measures to protect yourself from any future attacks.
Following these steps should help prevent your website from being hacked again, although remember that nothing you do will 100% guarantee that you won’t get hacked!
1. Remove any backdoors
If you haven’t already, then the first thing you should be doing is removing any backdoors or security holes in your WordPress website – unless you want to get hacked again!
You might not have identified every security weakness in your website, after all, you are only human. But any obvious security holes or backdoors that you’ve identified, or that your security software has highlighted, should be removed and patched up to avoid any further intrusions.
Keeping everything updated will also help avoiding any security exploits in your website.
2. Change the information in WP-Config.php
Since your website has already been compromised, there’s a chance they’ve had access to your wp-config.php file – and If they’ve had access, they could have easily copied over the information.
Effectively this means that they could still gain access to your system again unless you change this information.
In your wp-config.php file, you will want to change these areas of information:
- Security keys
- Salts
- Database Passwords
3. Harden your website
If your website’s been hacked then it’s a good sign that you need to harden your website and increase your website’s security.
There’s many different steps you can take to secure your website, which we’ve listed in detail earlier on in this article.
The most important thing you can do are installing a reliable Web Application Firewall, installing a good security plugin, and following good security practices.
4. Start a backup regime
Backing up your website frequently is always a good idea but at the end of the day it’s easy to forget about, and can have disastrous effects when your website is hacked.
Ideally you want to set up an automated backup regime for your WordPress website.
You want to make sure that all of your website’s data is being backed up regularly, ideally to a remote location for redundancy. After all, if a hacker has access to your website, they could just delete any local backups you have stored there.
There’s a lot of different backup plugins and services for WordPress including:
- UpdraftPlus – this plugin is the most popular free WordPress backup plugin with over 2 million websites using it. UpdraftPlus allows you to schedule automatic backups of your WordPress site to the cloud or to your local computer, as well as on demand.
- BackupBuddy – this is one of the most popular paid backup plugins for WordPress, allowing for scheduled backups to the cloud or locally, as well as on demand downloading of backups
- VaultPress – part of the Jetpack Backups software, this affordable plugin provides remote backups on a scheduled basis that can be automated

5. Serve static content rather than dynamic
The last area we will cover in our article is the benefit of serving static content over your website to your visitors rather than dynamic content.
If possible, try and serve your website in simple HTML files with CSS and JavaScript where needed.
When this is done, the server will send the requesting user the webpage as a file straight away, rather than building the page from various assets at the time of request.
Static web pages cannot be hacked or compromised as there’s no interaction with the code itself, so to speak. In this sense static content is much more secure than dynamic content, and gives you better protection against hackers.

